World Border Security Congress2017-03-22 14:49:25
Three Strategic Security Imperatives for Effective Migrant Control in the Age of Global Radicalization & Porous Borders
Let's face it: despite best intentions, billions of dollars spent, and the building of strategic coalitions, the current global migrant crisis continues. Both Turkey and the European Union continue to be faced with daunting numbers of irregular migrants comprised of refugees from the conflict areas in Syria and Iraq. There are a surprising number of migrants from Africa, economic migrants who are fleeing poverty from as far away as Pakistan and Bangladesh, and of greatest concern - a handful of radicalized individuals who are hiding in the crowds of true refugees as a cover to make their way into Europe to eventually commit acts of terror.
Numerous international security experts and politicians alike have publicly commented that the current migrant crisis in Europe is not going away by itself nor can it be fixed overnight. Moreover, the fact is that the current crisis cannot be resolved by today's conventional border security paradigms which worked for a period of time for the EU participants in the Schengen Agreement until the arrival of an external threat. Ironically, Albert Einstein’s observations of the world many years ago holds true for all developing nations today: "The world will not evolve past its current state of crisis by using the same thinking that created the situation."
Einstein's unique insight inspires the question ‘Why?'. Why is it that developed nations with stable and productive economies, strong military forces, and robust law enforcement, cannot effectively manage the waves of undocumented refugees nor identify terrorists who are literally walking into the heart of Europe?
It appears that the global security community might simply be asking the wrong question. The real question is - Why are millions of people able to leave their countries of origin in Africa and the Middle East, often passing through multiple countries along the way without any effective border controls and ultimately becoming part of a global calamity in the waters of the Mediterranean Sea?
The strategic answer is complex. Simply stated, effective border security can not begin on the shores or borders of Europe for the simple reason that humanitarian priorities trump strictly objective security measures in Europe. In the case of the European Union, the resulting dilemma is that a single member country is left with very few options as they try to balance humanitarian values, economic devastation, and domestic fears around terrorist attacks in their homeland and a myriad of related social concerns. To solve this problem, as Einstein’s adage conjectures, global security leaders should focus their efforts on how to establish effective controls for both legal and illegal travel at the point of origin from which an unwieldy blend of conflict zone refugees, economic migrants, and a handful of others with more nefarious objectives embark often with stolen or forged travel documents.
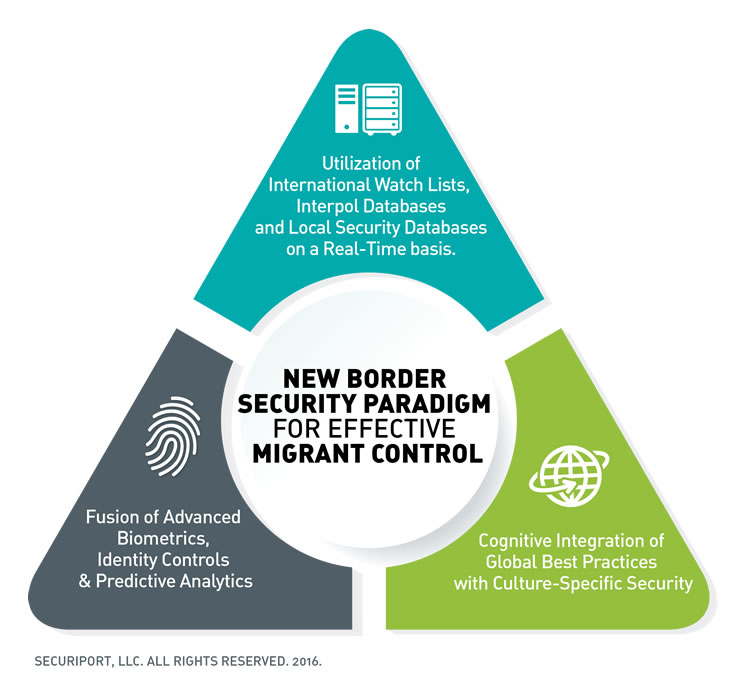
To succeed, global security leaders must plan and act proactively with a carefully integrated approach that incorporates behavioral, business process, high-technology security measures including biometrics, intelligent data analytics, and persistent surveillance, along with a strong localization and understanding of each developing nation where border security is an emerging or established risk factor. In other words, security leaders must adopt the following three strategic imperatives and integrate them into a powerful and practical solution.
1. Utilization of International Watch Lists, Interpol Databases and Local Security Databases on a Real-Time basis
While databases such as Interpol’s Stolen & Lost Travel Document (SLTD) database are regularly checked during the immigration process at most European airports, the majority of airports in developing nations around the world do not perform any data checks. Instead, the immigration systems in most countries typically are designed to collect data while ad hoc checks against watch lists and criminal databases is performed, if at all, long after the traveler has arrived or departed. In other cases, countries often put more resources on the risk assessment of travelers arriving in their countries while paying little concern to the screening and assessment of those departing. In either scenario, the outcome is potentially devastating as those travelers who may represent legitimate security risks are not properly screened. The key that decision makers must recognize is that technology and systems are readily available for the real-time identification and assessment of individuals who potentially represent a security threat.
2. Fusion of Advanced Biometrics, Identity Controls, & Predictive Analytics
While some developed nations have incorporated sophisticated biometric measures into their immigration control and migrant registration systems, many developing nations with little or no local resources still rely on primitive techniques and visual inspections to validate a traveler’s identity or to ascertain the authenticity of a travel document. The unfortunate fact is there are numerous false passports produced by criminal and terrorist organizations alike; and in some cases these false passports are even produced on authentic passports. The latter is the case with some Syrian and Iraqi passports from offices in areas under the control of ISIS. Consequently, the utilization of passport scanners which authenticate a travel document by checking the documents security features is inadequate. Similarly, the use of advanced biometrics on a stand-alone basis will not flag a potential person of interest. However, intelligent systems which combine biometric identity controls, travel document authentication, and structured database checks with predictive analytics raise the bar to 21st century standards and increase the likelihood of identifying members of terrorist and criminal organizations. Such predictive analytics, which are based on big data analytics of both structured and unstructured data through the utilization of behavior analysis, pattern recognition and profiling, are being used by some countries with very positive results.
3. Cognitive Integration of Global Best Practices with Culture-Specific Security that Respect and Recognize the Individual and Unique Behavior of Local Law Enforcement.
Securiport has been successfully working with several developing nations around the world, and has learned that no matter how many high-tech biometrics systems, video surveillance cameras, facial recognition analytics, and physical access control gates are placed in airports and seaports, the most strategically-important factor is understanding the local culture in the specific country of origin. Yes, law enforcement and border security officers share the same mission everywhere, but they are humans first and last. They have grown in their own cultures and use their local logic in assessing, identifying and dealing with security risks. Moreover, they prioritize risk differently than one might in Europe or in the United States. This common gap in security perspectives often results in a hole which terrorists, human smugglers, and other criminals can take advantage of. For this reason, technical security solutions must be complemented by adapted local situational awareness, business process rules, and cultural considerations. No nation is alike. No government is alike. No threat assessment is alike.
In order to prevent the next Paris, the next San Bernardino, the next Ankara, or next London, global security leaders must quickly adapt to the new integrated migration control paradigm by which one uses best practices from highly-proven security practices and technology. Best in class biometrics and predictive risk assessment technologies fused with comprehensive understanding of the local culture of the nation's customs, business processes, and culturally-sensitive law enforcement training that respects local values will do the most to eradicate security failures. In the absence of any one of the elements in this complex paradigm, there are holes which transnational criminals and terrorist organizations will take advantage of. However, in applying all three elements of this border security paradigm, one is likely to look at past tragedies and ask what else could have been prevented.
By Dr. Attila Freska is Chief Operating Officer of Securiport LLC and a recognized expert in the use of biometrics and predictive information systems for aviation security, immigration control and border security management applications
For more information contact:
Istanbul
-
Turkey
Tel: +442081445934